Our information security incident and privacy breach response policies and procedures provide well-defined, organized approaches for handling any potential threat to computers and data. They give frameworks for taking appropriate action when the source of an intrusion or incident at a third party is traced back to the organization. They also provide the steps to take in the event that protected health information (PHI) as defined by HIPAA, as well as all other types of personal information, is inappropriately accessed. These policies and procedures identify and describe the roles and responsibilities of the Incident and Breach Response Team, which is responsible for implimenting and following the procedures.
Information Security and Privacy Breach Policies and Procedures
If you need help creating a data breach policy or procedure for your business, then this document is for you. The information security incident and breach response policies and procedures contained within are fully customizable and extremely easy to complete. Just read through the document and fill in your organization's data as indicated. These policies and procedures support the following regulations and standards:
-
HIPAA 164.308 Administrative safeguards. (a)(6)(i) Standard: Security incident procedures
-
HITECH ARRA SEC. 13402. NOTIFICATION IN THE CASE OF BREACH.
-
NIST SP 800-66 Guide for Implementing the Health Insurance Portability and Accountability Act (HIPAA) 4.6. Security Incident Procedures
-
ISO/IEC 27002: 2005 Section 13 Information security incident management
-
ISO/IEC 27001: 2005 Section A.13 Information security incident management
-
The following sections of the February 2014 NIST Framework for Improving Critical Infrastructure Cybersecurity:
-
PR.IP-9: Response plans (Incident Response and Business Continuity) and recovery plans (Incident Recovery and Disaster Recovery) are in place and managed
-
DE.AE-5: Incident alert thresholds are established
-
RS.AN-2: The impact of the incident is understood
-
RS.AN-4: Incidents are categorized consistent with response plans Mitigation (RS.MI): Activities are performed to prevent expansion of an event, mitigate its effects, and eradicate the incident.
-
RS.MI-1: Incidents are contained
-
RS.MI-2: Incidents are mitigated
-
RS.MI-3: Newly identified vulnerabilities are mitigated or documented as accepted risks
-
-
COBIT 5 APO12.06
-
COBIT 5 DSS04.03
-
ISA 62443-2-1:2009 4.2.3.10
-
ISA 62443-2-1:2009 4.3.2.5.3, 4.3.4.5.1
-
ISA 62443-2-1:2009 4.3.4.5.6, 4.3.4.5.7, 4.3.4.5.8, 4.3.4.5.10
-
ISA 62443-3-3:2013 SR 5.1, SR 5.2, SR 5.4
-
ISO/IEC 27001:2013 A.12.2.1, A.16.1.5
-
ISO/IEC 27001:2013 A.12.6.1
-
ISO/IEC 27001:2013 A.16.1.1, A.17.1.1, A.17.1.2
-
ISO/IEC 27001:2013 A.16.1.4
-
ISO/IEC 27001:2013 A.16.1.5
-
ISO/IEC 27001:2013 A.16.1.6
-
NIST SP 800-53 Rev. 4 CA-7, RA-3, RA-5
-
NIST SP 800-53 Rev. 4 CP-2, IR-4, IR-5, IR-8
You will receive a customizable DOCX file similar in format to the one found under our free resource page. Feel free to contact us if you have any questions.

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
Information Security and Privacy Breach Response Flow Charts
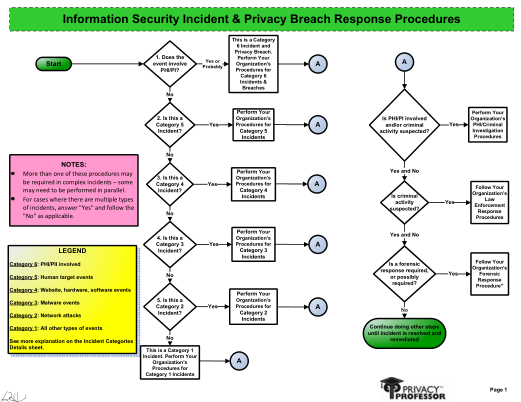
This set of information security incident and breach response flow charts can be used by any type of organization in any industry. Visual aids such as flowcharts are a great addition to the implimentation of policies and procedures.

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
Information Security and Privacy Breach Policies and Procedures AND Flow Charts
This package includes both of the above products at a discounted rate.

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
Vendor Inventory
Do you know all the vendors who have access to, or store, your business and personal data?
Do you know all the vendors who have access to your systems where work activities occur?
Do you have all the vendors documented?
If you have not documented every third party that has any type of access to, or stores, your organization's information and systems, then you could have significant information security and privacy risks that you aren't aware of. And, you may be in violation with one, to many, legal compliance requirements.
Organizations must document all types of vendors that they to perform business activities on their behalf to be able to effectively manage their vendor risks, to support vendor management compliance requirements, and also to demonstrate due diligence to regulators, auditors, and business clients.
The first step in vendor management is establishing a vendor inventory of all third parties with any type of access to business and personal information from your organization. Keep this inventory updated.
Then, use this inventory to identify where regulated data is located, to support timely and regulated breach response activities, to demonstrate due diligence, and to determine when new risks emerge. In addition to many other benefits.
Our vendor inventory provides the first step for you to take in effectively managing your third parties. It also is beneficial for improving your existing vendor management activities that do not include a vendor inventory.
Includes both Word and Excel format.
Our regular price is $49.99 for both formats of this tool. However, we understand that during these difficult times many organizations are addressing their information security and privacy obligations on limited budgets, so for a limited time we are making the vendor inventory available for $24.99.
Row #1 provides an example of the type of information to put each row.
Would you like to speak with Rebecca Herold, internationally recognized information security, privacy and IT expert, about your vendor management program? How to establish your inventory? Other related information security and privacy topics?
We are also discounting our hourly phone consultation during this time. Our regular phone consulting rate is $195/hour. For a limited time we are reducing our hourly rate for those who purchase the vendor inventory to $125/hour.

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.

