IoT Security and Privacy
October 2021 IoT Security and Privacy Infographic
Cybersecurity for Grandparents (And Everyone Else!): Q4 2021 3-Volume Set of Flipbooks
Volume 4: Securing Smart Homes
Volume 5: Securing IoT On the Go
Volume 6: Coming Soon! Will be published in November, 2021! Check back, or request notification from: info@privacysecuritybrainiacs.com
See the Privacy & Security Brainiacs page dedicated to IoT news for a wide range of past and current real-life examples here: https://privacysecuritybrainiacs.com/resources/news/IoT
Each environment where IoT products are used needs to have risk mitigation controls implemented as appropriate to the associated digital ecosystem to most effectively mitigate the most cybersecurity and privacy risks. However, most consumers, and businesses with no IoT product cybersecurity or privacy experts on staff or contract, simply aren’t aware of how to determine these risks.
We are here to help you most securely implement and use your IoT products!
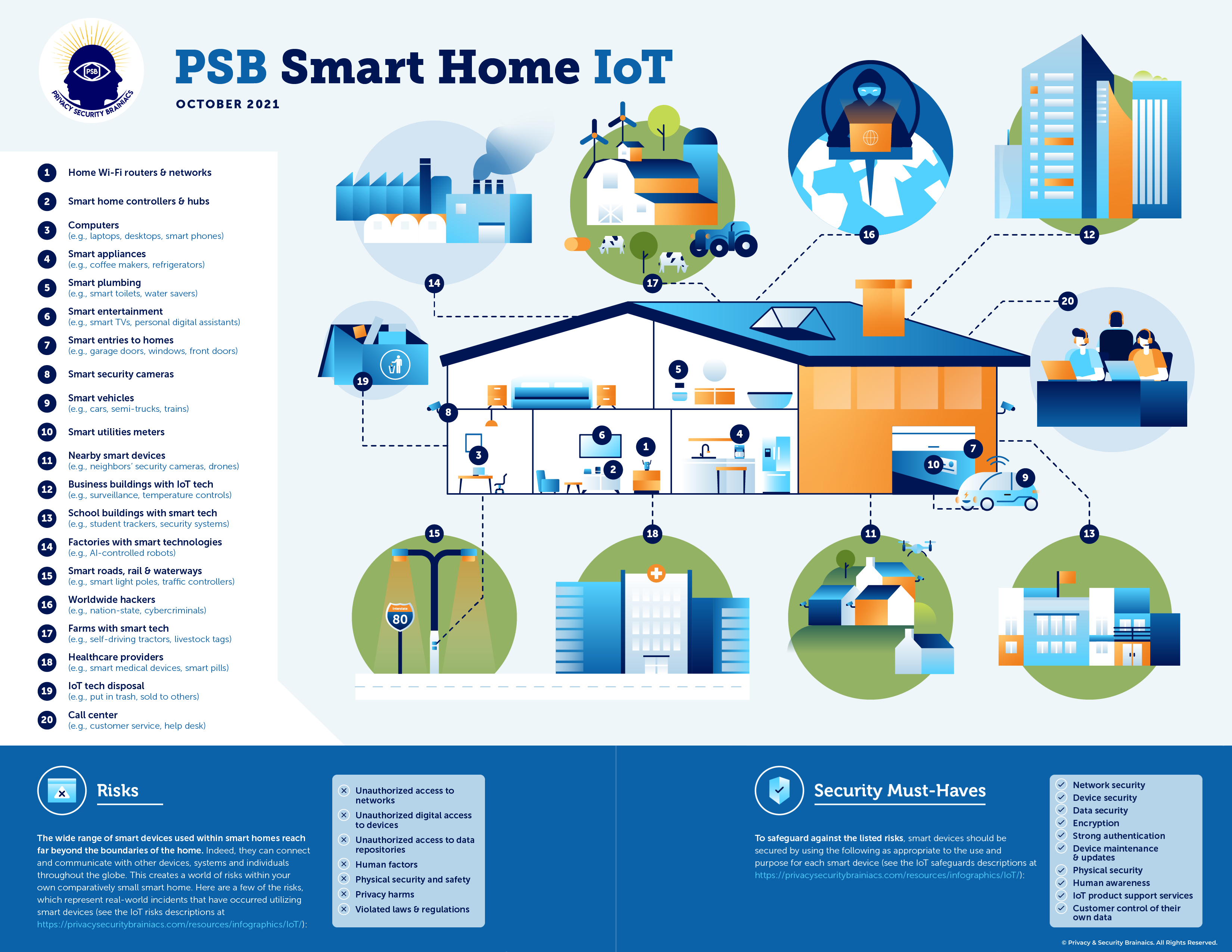
Here is a list of common types of risks, as shown in the PSB Smart Home IoT infographic, and associated examples. Below the risks is a list of key security actions and tools, listed in the PSB Smart Home IoT infographic, that can be implemented to significantly improve cybersecurity and privacy protections to dramatically mitigate the risks. These are not comprehensive lists possible risks and associated security must-have mitigations to take. However, if time is taken to implement even just one or two security and/or privacy controls, these would be the ones we’d recommend you take. Of course, we hope you would then consider implementing more security must-haves, to more comprehensively protect your IoT products and connected networks, along with protecting your privacy.
IoT Risks
The following risk descriptions and examples supplement the information within the PSB Smart Home IoT Infographic, providing just a few real-life examples of how weakly secured IoT products have created risks that were exploited by cyber criminals, snoops, and others. Many more details can be found in our book, “Cybersecurity for Grandparents (And Everyone Else!): Q4 2021 – IoT Security and Privacy,” which will be published by the end of November, 2021.
- Unauthorized access to networks. Access can be made into Wi-Fi networks through security vulnerabilities within IoT products. Weakly secured networks can also allow access into IoT products attached to the networks. Hackers from anywhere in the world can discovered these vulnerabilities and exploit them. For example, multiple vulnerabilities were identified within in a widely-used baby monitor product. Some of the vulnerabilities allowed unauthorized cyber snoopers access to the Wi-Fi networks to which the devices were attached, allowing the digital interlopers and hackers to scan for more vulnerabilities on the networks. This created risks for a wide range of harms to the associated individuals, including access to the network users’ data files, videos, photos, and other IoT devices. The network access also allowed access into the other connected networks, including the business networks used by the inhabitants for remote working, and the school systems being used for remote learning.
- Unauthorized digital access to devices. Security vulnerabilities, both technical and non-technical, can allow for access into the device itself, and subsequently allow for device settings changes, collection of data through the device, communications through the device, and other activities, which can also result in a wide variety of harms to those using the IoT products. For example, millions of attacks on IoT devices have been occurring from IoT Marai malware botnet variants from as far back as at least 2016. In 2016 it was determined that 40,000 active and online IoT devices had been infected by the Marai botnet, and approximately 2.5 million offline IoT devices were infected, with around five IoT devices becoming newly infected every minute. Examples of a few of the types of IoT devices impacted included air-quality monitors, personal surveillance cameras and home routers. The devices were located in consumer homes, business buildings, schools, government agencies, and generally all other types of organizations that choose to implement them. IoT Marai variant botnet attacks from October 2019 through June 2020 increased 400% compared to the total number of IoT attacks in the previous two years. The range of impacts from the Marai botnet attacks included launching from the IoT devices the following types of attacks: distributed denial of service (DDoS) attacks (through UDP flooding, HTTP flooding, TCP flooding); application-layer attacks; volumetric attacks; TCP state-exhaustion attacks; and logic bombs.
- Unauthorized access to data repositories. Unauthorized access into the data repositories of consumers, as well as into business networks and other types of organizations’ networks, can occur through vulnerabilities in IoT products. For example, in 2017, a hacker located in Finland was able to gain access to a Las Vegas, Nevada, casino network through the IoT fish aquarium that the casino had installed in their casino. Among other “smart” components, the aquarium had a smart thermostat that automatically adjusted the water temperature, and a smart water sensor that reported when water quality was dangerous for the marine life within. Hackers found the smart aquarium thermostat from the other side of the world, and were able to easily determine that there were no access restrictions in the IoT product, and after they got into the product, they saw there were no digital roadblocks to and through the network to which the aquarium was attached. The hackers stole 10 GB of sensitive data from the casino’s network.
- Human factors. Those involved with not only using the IoT products, but also those who support the products, such as the manufacturers’ customer support call centers, and those who design the IoT products and make mistakes, or create digital holes within the devices or plant malicious code, also create risks to those using the IoT devices. This is a huge concern, because any technology can be defeated by human actions if appropriate controls and oversight are not in place. This is why is it equally important for manufacturers to have strong non-technical controls in place (education, procedures, policies, etc.) as well as building strong technical security and privacy controls into IoT products and all other types of technologies. For example, our PSB CEO was an expert witness in a case where lack of properly followed identity verification by the contracted customer support call center for the manufacturer’s IoT device controller and app access resulted in woman being assaulted to near death by a stalker she was hiding from in a hotel. The victim had seen activity in her smart car dashboard and logs and suspected the stalker was getting into her account. Even though she asked the call center, upon three different occasions prior to the assault, to not allow anyone other than herself access to her smart car information, they did. Our CEO was able to confirm through the car logs, IoT product mobile app logs, and the controller and hub logs, along with the few recorded customer support phone calls that the customer support contracted entity provided that the support staff went ahead and gave the stalker access after he used social engineering multiple times to trick the customer support staff, even after the car owner literally begged the customer support staff during phone calls to disable her account because she feared for her life. The customer support business had very weak identity access procedures, did not log all the requests, may not have kept all the recordings of calls, did not have training for social engineering, among many other problems.
- Physical security and safety. Weak technical and non-technical security and privacy controls can impact the physical access to the associated IoT device users, and result in subsequent physical harms. The previous example demonstrates this risk along with the human factors. As another risk example, a large number of fitness trackers used apps to track and create online heatmaps of the activities of users of a wide range of fitness trackers. They displayed over 1 billion activities online, including running and cycling routes. An option in the fitness apps and controllers existed to allow fitness tracker users to mark their data as private, so it would not be posted online. However, there bugs in the software that resulted in the fitness tracker users having their routes and locations published in the heatmaps, even when they had configured the IoT fitness tracker app settings to keep their data private, and they believed their locations would not be published. There were other security vulnerabilities in the way the apps were engineered allowed anyone to access this type of information online with a simple URL edit. This included access from published information showing locations and exercise routes of the users of the fitness tracker apps, and showing these activities over periods of several years. These unwanted revelations have occurred multiple times, including when military personnel had their data posted online, despite the users configuring the devices and apps to keep the data private. Locations of all those working at government or military installations can quickly become national security risks in such situations.
- Privacy harms. IoT products broadly record a wide range of activities that occur in the vicinities where they are located and used. This has resulted in many situations where recordings are made of what people were saying and doing, when the IoT product users did nothing to activate the recordings. For example, in the past ten years there have been multiple times when smart TVs have not only been discovered to be recording what the TV users are watching, but they were also recording what those in the vicinity were saying, and making videos to determine how those in the vicinity were reacting to the shows that being broadcast. That information was being used to market to those being recorded, to customize the ads and shows they would see, and other activities. It was also discovered that those recordings and associated data was often being shared with third parties, often being sold for large amounts of money. TV manufacturers have paid penalties from regulatory agencies for the privacy violations. Smart toys have also been discovered to be making similar types of recordings over the past decade.
- Violated laws & regulations. Not only do the manufacturers face violating data protection and privacy laws and regulations by not providing required privacy protection capabilities within IoT products, but the organizations that use them, and even general consumers using them, face lawsuits and significant fines and penalties for breaking laws and regulations. For example, a security system customer in the UK installed security cameras throughout his property. The images and audio captured included a portion of his neighbor’s property. There was no capability to turn off the recording of such images and audios in the security system. The neighbor sued the security system customer for making such recordings, in violation of the UK Data Protection Act and the EU General Data Protection Regulation (GDPR). A judgment of a £100,000 (approximately USD $136,000) fine was made against the IoT product security system customer.
IoT Security Must-Haves
The following security tools and actions supplement the information within the PSB Smart Home IoT Infographic. Many more details for these security tools and actions can be found in our book, “Cybersecurity for Grandparents (And Everyone Else!): Q4 2021 – IoT Security and Privacy,” which will be published by the end of November, 2021.
- Network security.
- Use strong authentication to the Wi-Fi router and network.
- Use the strongest network encryption available.
- Enable automatic software, firmware and security updates from the manufacturer.
- Use a firewall on your network.
- Limit network availability to the IoT devices.
- Create a separate Wi-Fi network just for your IoT devices if at all possible.
- Make sure the manufacturer has security and privacy instructions and provides customer support.
- Device security.
- Use device anti-malware tools.
- Use firewalls on the network devices.
- Use VPNs on your computing devices.
- Use strong authentication to networked computing devices.
- Strongly encrypt data stored within the devices.
- Data security.
- Use access control capabilities.
- Encrypt data.
- Delete data no longer needed.
- Encryption.
- Use no less than WPA2 Advanced Encryption Standard (AES) encryption on routers, but use WPA3 encryption where available.
- Strongly encrypt data in storage, using AES encryption.
- Encrypt data transmitted from the device. Good options include RSA and SFTP.
- Strong authentication.
- Use multi-factor authentication (MFA).
- Use biometric authentication where available and practical.
- Use long and complex passwords where passwords are required.
- Device maintenance & updates.
- Enable automatic software, firmware and security updates from the manufacturer.
- Sign up for updates when installing your product.
- Request updates from the manufacturer’s website.
- Call the manufacturer’s customer service number and ask how to get these.
- Physical security.
- Keep IoT device controllers with display screens secured from unauthorized viewing.
- Keep IoT devices and components physically secured.
- Remove all data and software when no longer using the IoT device and/or components.
- Human awareness.
- Ask the manufacturer for IoT product security and privacy training.
- Ensure the manufacturer provides documentation about the IoT device security and privacy capabilities and how to use them.
- Ensure the manufacturer requires their support staff to take security and privacy training, and to enforce separation of duties to prevent malicious actions and to catch mistakes.
- Take Privacy & Security Brainiacs training (free and/or paid) covering IoT security and privacy.
- IoT product support services.
- Manufacturer should have a documented procedures for customers to follow to ask questions about security and privacy.
- Manufacturer should have a documented procedures for customers to report security and privacy problems.
- Manufacturer should provide software, firmware and hardware updates to IoT product customers for newly discovered security and privacy holes and problems.
- Customer control of their own data.
- The manufacturer’s website should have a privacy notice describing the control that customers have over their own associated data used and collected by the IoT product.
- Manufacturers should describe the capabilities and procedures to allow customers to delete their associated data.
- Manufacturers should describe the capabilities and procedures to allow customers to correct their associated data.
Many more details can be found in our book, “Cybersecurity for Grandparents (And Everyone Else!): Q2 2022 – IoT Security and Privacy,” which will be published in Q2 2022.
Privacy & Security Brainiacs offers a wide range of security and privacy training, tools and consulting. We are also happy to work with you directly to help you better understand how to use these types of security and privacy controls. If you need more information, or help, please get in touch with us using: info@privacysecuritybrainiacs.com