In 2015 I wrote a blog post as part of the Dell Insight Partners program that provided a theory about how Eddie Tipton committed the largest lottery fraud in US history, based on the information that had been publicized about that case at that point in time. Tipton was the Information Security officer for the Iowa-based Security Director of the Multi-State Lottery Association at the time he was arrested. The fraud has often been referenced as the Hot Lotto fraud. That blog post follows below the line.
So, how accurate was I with my theory? I recently had the opportunity to speak with Rob Sand, the current Auditor for the State of Iowa who was Assistant Attorney General for the State of Iowa at the time and who successfully prosecuted Eddie Tipton. You can hear my discussion with Rob about the details of how Tipton rigged the lottery drawings, through his trusted access to the lottery technology, and how Rob was able to success fully prosecute him, in my April Voice America episode of Data Security and Privacy with the Privacy Professor which first airs on Saturday, April 4 at 11:00am Eastern Time. The recording will be available upon demand after the initial airing.
I started my career as a systems engineer at a large multinational financial and healthcare corporation. I was responsible for creating and maintaining the applications change management system on an IBM/390. The purpose of the system was to ensure that after the programmer finished coding, the code could be moved, with the approval of the manager, to a different area to test. After testing was complete it would be moved back to the development area if changes were needed, or a different manager would approve it to be moved to the live/production area for widespread use.
By requiring different individuals/roles other than the programmer (who did her own testing while creating the program) to test the program, it accomplished two primary goals:
-
ensure the program truly worked as intended (did not include any unintentional mistakes), and
-
ensure no backdoors, logic bombs, or otherwise nefarious activities were included within the code that could lead to fraud, or other malicious activities (did not include intentional wrong-doing).
This initial project is what got me interested in information security; through it I discovered the many ways in which some of the programmers would try to get around the controls I had built into my change control system.
Organizations must Still Address Insider Threats
The need for such internal controls within computer systems, physical security controls, and administrative procedures, to mitigate the insider threat, has existed since at least the 1950’s when organizations widely started using computers, and there have been some spectacular fraud committed since by insiders with trusted access to systems and security controls. Consider the case that was the subject of the 1978 James Woods movie, The Billion Dollar Bubble, which chronicled the two billion dollar insurance embezzlement scheme, using fraudulently modified computer code, involving Equity Funding Corporation of America. I’ve shown this movie upon several occasions to clients for information security awareness events.
A fraud investigator friend told me long ago that there will always be 10% of folks who will try to do fraud (or other bad things for that matter), and 80% who will do bad things under circumstances where they feel justified in doing so. The Medco Health Solutions, Inc. computer systems administrator who was indicted for attempting to disable his employer’s corporate computer servers through the use of a concealed malicious software program (a logic bomb) is just one of many examples of this 80%.
There was recently a trial in Iowa for the Security Director of the Multi-State Lottery Associationaccused of using his authorized access and job responsibilities to commit fraud to collect a $14 million Hot Lotto prize. This is yet another instance of an insider with an extremely large amount of authorized access to systems, and physical access to computer hardware, who apparently could not resist the temptation to use that access for his own personal gain. I recently provided a high-level description on the Great Day KCWI 23 morning show of how the Security Director may have pulled off this elaborate fraud.
This incident is a great case study to learn about a variety of risks involved with the insider threat.
First let’s consider some key points involved with this convicted fraud attempt:
- Unlike other types of Lotto drawings which use balls, Hot Lotto numbers are generated randomly (determined by flipping a coin) using one of two stand-alone computers each running a software program that uses a random number generator. This creates the need for those systems to be as tamper-proof as possible, and to have compensating controls for those who have access to them.
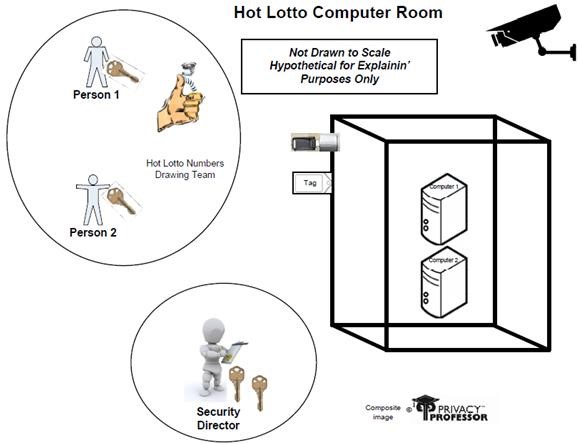
Figure 1
-
There are many security controls around the Hot Lotto computers used for the random number generator and for the event itself (see Figure 1 for a graphical representation).
-
The computers are located in a secured room that reportedly only 5 people have access into. (The Security Director, Eddie Tipton, was one of those five.)
-
The two computers used to generate the winning numbers are stand-alone computers; meaning they are not connected to any other computer, including no by wireless connectivity.
-
The computers are located in a secured container in the secured room that can only be opened using two keys, and a seal is place on the container to indicate if it has been tampered with. Two people, each with a key, must open the cabinet to start the Hot Lotto winning number program on lottery nights.
-
A closed circuit camera records all activities within the room. Those same five people are reportedly the only ones with access to the camera controls.
-
-
Prosecutors claimed Tipton entered the Hot Lotto draw room on November 20, 2010, ostensibly to change the time on the computers (daylight savings time had ended November 7). Interestingly the cameras on that date recorded only one second per minute rather than running continuously like normal.
-
The case was made to support the theory that Tipton used his privileged and authorized physical access to the two Hot Lotto computers to surreptitiously install a root kit (which he had significant knowledge about), that rigged the US$16.5 million drawing held on December 29, 2010, into them via a USB drive; which theoretically could have been done during those 59 unrecorded seconds each minute that he was in the room.
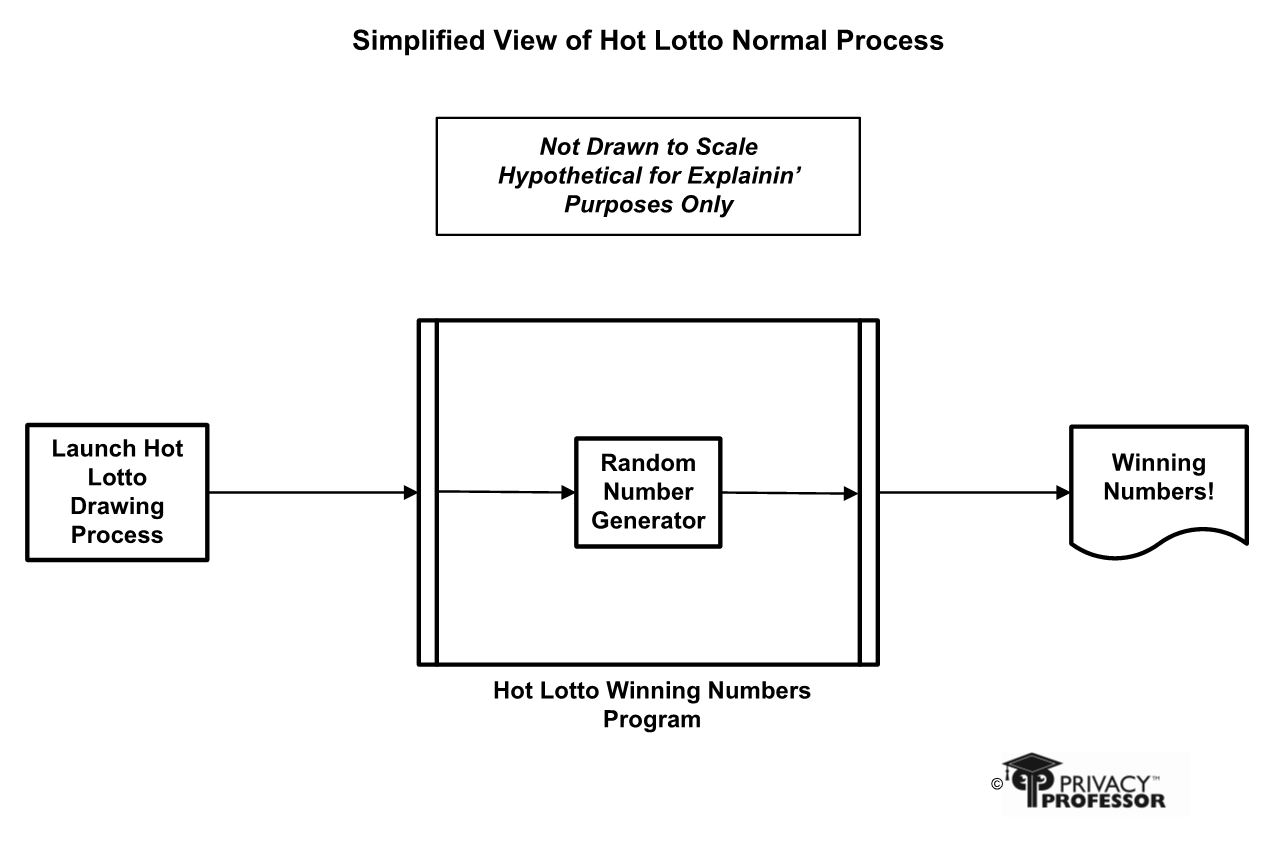
Figure 2
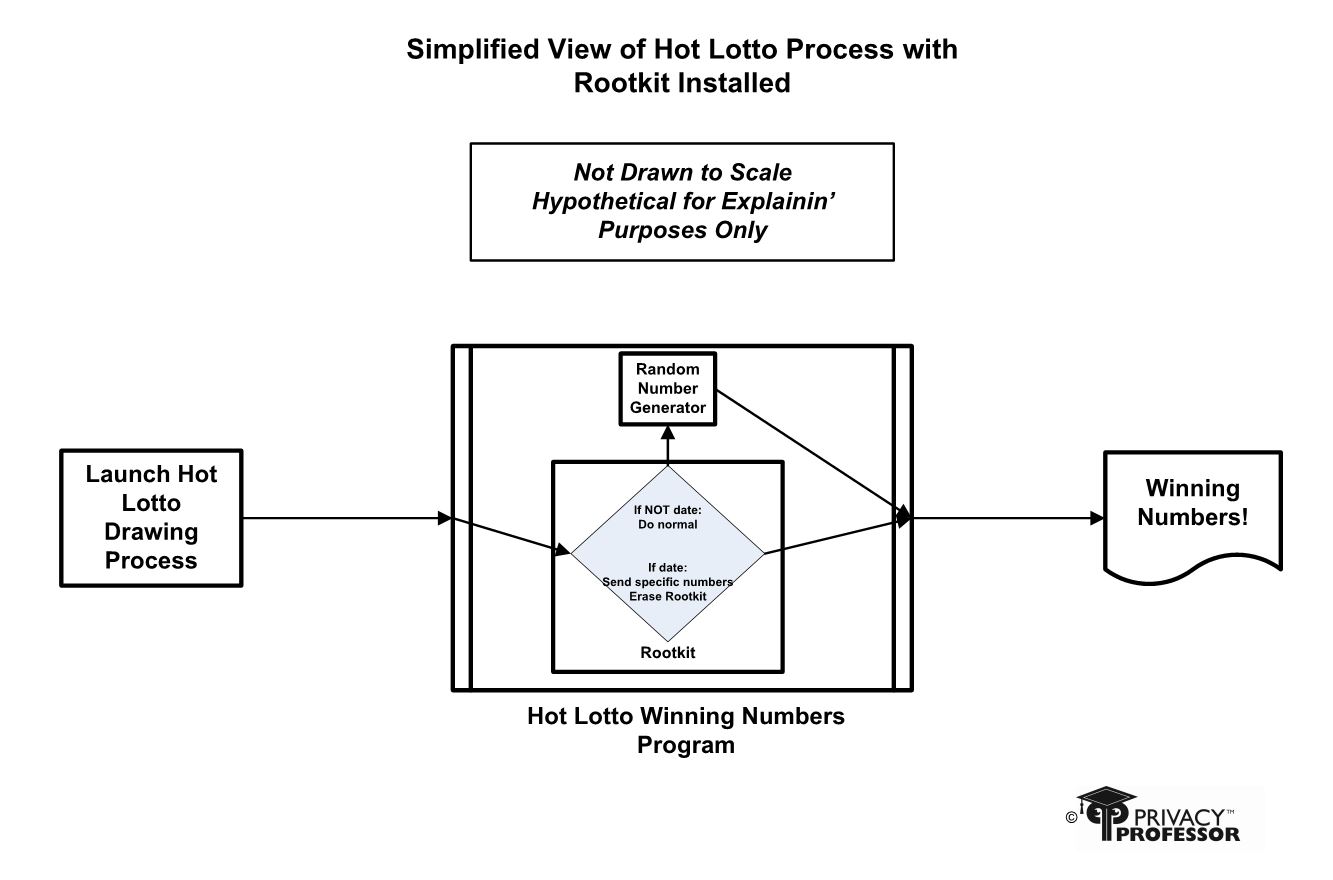
Figure 3
-
Figure 2 is my simplistic representation of how the program typically ran. Fairly straight forward. My hypothesis is that Tipton installed a rootkit that checked for the date when the program was initiated, and then diverted the program to choose his specifically chosen numbers instead of going to the random number generator as usual, as represented in Figure 3. Then the rootkit completely deleted itself to remove all digital evidence on those computers soon after the scheduled drawing.
-
Witnesses testified it was Tipton, wearing a hoodie and disguise that was on video that showed him purchasing the ticket containing the rigged numbers from a convenience store in Des Moines, even though he claimed he was in Texas at the time.
-
No one claimed the winnings for that ticket until nearly a year later. Then the “winning” ticket of the draw was routed through several accomplices, including a Belize-based investment trust that claimed to represent its owner, in an attempt to claim it anonymously, but the prize claims were rejected per Iowa Lottery policy forbidding anonymous claims (another good administrative procedural control to have in place).
-
By means of a person from Quebec City identified as the trust’s president, the trust was found to be connected to two people from Sugar Land, Texas, including Robert Rhodes, with whom Tipton had professional relations, had contact with, and was determined to be in Des Moines during the period that Tipton had purchased the ticket.
-
Based upon Tipton’s significant physical, administrative and technical access to the lottery computers in the secured room, his bad disguise and catching him in a lie on video, his demonstrated expertise in the use of rootkits, his associations with those in the trust, and some other associated facts, he was found guilty of attempted fraud.
After the fraud, the Multi-State Lotto Association made several additional changes to improve upon what were strong administrative, physical and technical safeguards, at least for trusted employees, to also mitigate the insider threat of those with trusted access who may go rogue. At a high level those additional controls included:
-
Adding the ability to check for rootkits installed in the lottery systems, as part of security updates.
-
Replacing equipment and software used in the drawings, including the security cameras that monitor the drawing room. This way even if Tipton had given information about them to others, it would not do them any good.
-
Introducing additional separation of duties for employees. Details of this were not provided, but if I were making recommendations to them some would include:
-
Not allowing the persons authorized to be in the room to also have access to the camera controls, which supports separation of duties controls.
-
Implementing access and activity logs on the computer systems that those with access into them within the room do not have access to view or change.
-
Requiring an additional person to closely observe the activities of those making changes to the computer systems that are not in the same department.
-
Establish Controls to Mitigate Insider Threats
The bottom line is that organizations must still address insider threats, even with so many other new and emerging data security threats and vulnerabilities that they have to contend with on a daily basis.
Always remember: when giving personnel access to data security and privacy controls, it is imperative that other controls exist to ensure that trusted access is not exploited for the bad to help keep the 10% of those with trusted access who are always going to try and do bad things, and the 80% who are trusted but will do bad under certain circumstances, from taking advantage of their extensive data and systems access capabilities to commit fraud, or other crimes and malicious acts.
This post was written as part of the Dell Insight Partners program, which provides news and analysis about the evolving world of tech. Dell sponsored this article, but the opinions are my own and don’t necessarily represent Dell’s positions or strategies.

